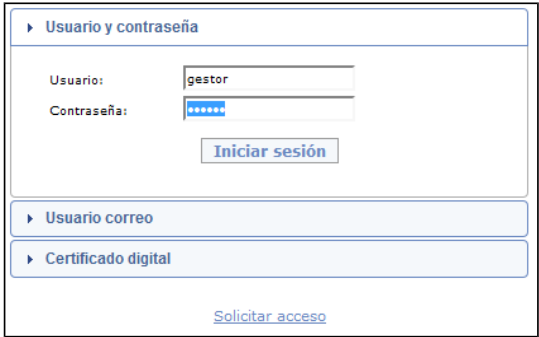
Authentication to the system is carried out either by one of the three systems supplied by the tool (electronic certificate, LDAP and user/password) or by adapting to an existing authentication system in the corporation (own single sign on).
After authentication, the information on the user is supplemented with all the information relating to their visibility of procedures and data. All of this is based on option profiles, maps of transitions of authorised procedures to the user and bias of information associated with the user (restrictive filters).